It's a rather common scenario, you know, when your remote IoT devices just aren't connecting quite right to your AWS Virtual Private Cloud (VPC). It can feel like a real head-scratcher, especially when you've put in all that effort to set things up. That, honestly, is a very frustrating spot to be in for anyone working with connected gadgets and cloud infrastructure.
For many folks, getting these clever little devices to chat securely with your private cloud space in AWS can seem a bit like trying to solve a puzzle with missing pieces. There are so many moving parts, from network configurations to security policies, and it’s easy for something to get slightly out of whack. This guide, you see, aims to help you untangle those knots and get your remote IoT setup talking smoothly and safely to your AWS VPC.
We’re going to walk through some of the typical reasons why you might be hitting a wall when you try to securely connect remote IoT VPC AWS not working. We’ll also cover some practical steps to get things back on track, and then, a bit later, we'll share some good practices for keeping your connections strong and secure moving forward. So, let's get into it, shall we?
Please note: The "My text" provided to me, which discusses financial budgeting, Excel operations, Word document formatting, and video editing, is completely unrelated to the topic of securely connecting remote IoT devices to AWS VPC. Therefore, it cannot be used as a reference for the content of this blog post. This article will focus solely on the AWS IoT connectivity challenge.
Table of Contents
- Understanding the Challenge: Why It's Tricky
- Common Roadblocks When Securely Connecting Remote IoT to AWS VPC
- Essential Troubleshooting Steps
- Best Practices for Secure IoT-VPC Connections
- When All Else Fails: Seeking Deeper Help
Understanding the Challenge: Why It's Tricky
Connecting remote IoT devices to an AWS VPC, especially when it needs to be secure, is a rather intricate dance. It’s not just about getting a signal through; it’s about making sure that signal is protected, authorized, and goes exactly where it's supposed to. The sheer number of components involved, you know, can make it a bit overwhelming. You have the device itself, its network environment, the internet, AWS IoT Core, and then your VPC with all its networking layers. It’s a lot to keep track of, frankly.
One of the big reasons this can be a puzzle is the distributed nature of IoT. Your devices are out there in the real world, perhaps in homes, factories, or even far-flung fields. They need to talk to a centralized cloud environment that's designed for privacy and control. Bridging that gap securely requires careful planning and, sometimes, a bit of detective work when things aren't working as expected. That, in some respects, is where many folks get stuck.
- Kalogeras Sisters House Location Google Maps
- Wentworth Miller Net Worth
- Nicoleponyxo Nude
- Chynna Phillips
- Roddy Mcdowall
Security, too, is a primary concern here. You’re not just trying to get data from point A to point B; you’re trying to do it without exposing sensitive information or creating vulnerabilities. This means layers of encryption, proper identity management, and network isolation. When any of these layers has a tiny hiccup, it can lead to a complete breakdown in communication, making your attempt to securely connect remote IoT VPC AWS not working.
Common Roadblocks When Securely Connecting Remote IoT to AWS VPC
When your remote IoT setup isn't quite clicking with your AWS VPC, there are a few usual suspects that tend to cause trouble. It's often not one big thing, but rather a combination of smaller misconfigurations that add up to a connection headache. We'll go through some of the most frequent ones, so you can start to pinpoint where your particular puzzle might lie. You know, it's often the little details that trip us up.
Network Configuration Glitches
This is probably one of the most common areas where things can go awry. Inside your AWS VPC, you have security groups and network ACLs (NACLs) that act like digital bouncers, deciding what traffic gets in and what stays out. If these aren't set up just right to allow traffic from your IoT devices, then, well, nothing gets through. You might also have issues with routing tables not knowing how to direct traffic to or from your VPC endpoint, or maybe even a subnet that isn't properly associated. It's a bit like having a locked door with no key, really.
For example, you might forget to open up the correct port (like 8883 for MQTT over TLS) in your security group that's attached to your VPC endpoint. Or, perhaps, your NACLs are too restrictive, blocking both inbound and outbound traffic that your IoT devices need. It’s a very common oversight, yet it stops everything cold. This can certainly lead to a situation where securely connect remote IoT VPC AWS not working.
VPC Endpoint Issues
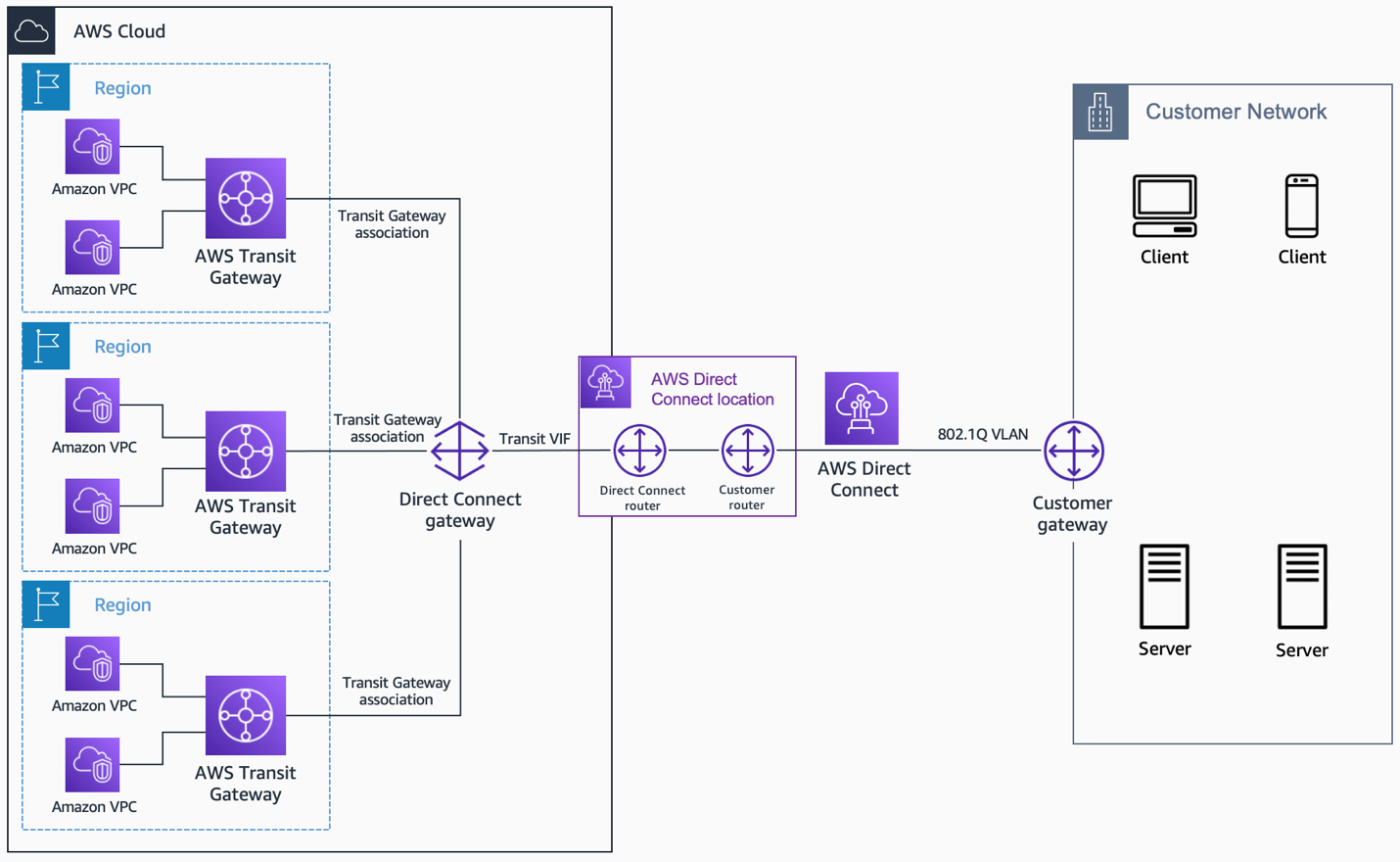
VPC endpoints are pretty neat because they let your devices connect to AWS services privately, without needing to go over the public internet. But if your VPC endpoint for AWS IoT Core isn't configured correctly, or if its DNS resolution isn't working as it should, then your devices won't know where to send their messages. Sometimes, people create the endpoint but forget to associate it with the correct subnets, or they might pick the wrong type of endpoint. That, too, can cause a lot of confusion for your devices trying to find their way.
You might find that your devices are trying to reach the public AWS IoT endpoint instead of your private VPC endpoint, simply because their DNS isn't resolving the private IP address. This is a subtle but significant issue. Or, perhaps, the security group attached to the endpoint itself isn't allowing connections from your devices' source IP ranges. It's a critical piece of the puzzle, and if it's off, it definitely means securely connect remote IoT VPC AWS not working.
Device-Side Woes
Sometimes, the problem isn't with AWS at all; it's right there on your device. Things like incorrect certificates, expired certificates, or even the wrong root CA certificate can prevent your device from establishing a secure TLS connection. If the device's firmware is outdated or has a bug, that can also cause connection failures. And, of course, basic network connectivity on the device itself – like a weak Wi-Fi signal or an improperly configured cellular modem – can stop things before they even start. You know, the device has to be ready to talk, too.
Imagine your device has a certificate that doesn't match what AWS IoT Core expects, or maybe it's using an old security protocol that's no longer supported. These little discrepancies, seemingly minor, can completely derail the secure handshake process. It's really about ensuring the device's identity and communication methods are perfectly aligned with the cloud's expectations. This is often where securely connect remote IoT VPC AWS not working originates.
IAM Permissions
AWS Identity and Access Management (IAM) is how you control who can do what in your AWS account. If the IAM policy attached to your IoT device's certificate or thing isn't granting the right permissions – like the ability to publish messages or subscribe to topics – then even if the connection is established, the device won't be able to perform its intended actions. It's like having a valid ticket to a concert but not being allowed to enter the venue, basically. This is a very common source of silent failures, where everything looks connected but no data flows.
You might have a policy that only allows publishing to a specific topic, but your device is trying to publish to another. Or, perhaps, the policy is missing the `iot:Connect` permission, which is absolutely essential for the device to even initiate a connection. These permission hiccups are rather tricky because they don't always manifest as a clear "connection failed" error, but more as a "nothing is happening" scenario, which can be quite puzzling.
Firewall and Proxy Hurdles
If your remote IoT devices are sitting behind a corporate firewall or an outbound proxy server, these network components can definitely interfere with connections to AWS. Firewalls might block the necessary ports, or proxies might not be configured to allow the specific protocols (like MQTT) that IoT devices use. This is particularly true in industrial settings or enterprise environments where network security is very strict. You know, sometimes these on-premise safeguards are just doing their job a little too well for your IoT needs.
Consider a situation where your device needs to reach a specific port on the AWS IoT Core endpoint, but the local network's firewall is simply dropping all traffic on that port. Or, perhaps, your proxy server requires specific authentication that your IoT device isn't providing. These external network elements are often overlooked, yet they can be the primary reason why securely connect remote IoT VPC AWS not working, despite perfect AWS configurations.
Data Flow and Protocol Mismatches
While not strictly a "connection" issue, sometimes the problem is that data isn't flowing correctly even after a connection seems to be made. This could be due to protocol mismatches (e.g., your device sending HTTP when AWS IoT Core expects MQTT), incorrect topic names, or malformed payloads. AWS IoT Core has specific expectations for the data it receives, and if your device isn't meeting those, then your data won't be processed. It's like trying to speak a different language, really; the connection might be there, but the message isn't understood.
For instance, if your device is publishing to a topic that doesn't have any rules associated with it in AWS IoT Core, the message might be received but then simply dropped without further action. Or, perhaps, the message payload isn't valid JSON, causing parsing errors. These are subtle issues that can make it seem like the connection itself is faulty, when in fact, the communication content is the actual snag. This can certainly make it appear that securely connect remote IoT VPC AWS not working, even when a basic connection exists.
Essential Troubleshooting Steps
When you're faced with the puzzle of securely connect remote IoT VPC AWS not working, a systematic approach is your best friend. It's like being a detective, gathering clues and eliminating possibilities one by one. Don't just guess; follow these steps to methodically uncover the root cause. This methodical way, you know, really helps clear things up.
Verify Network Pathways
Start by checking the most basic network connectivity from your device. Can it reach the internet at all? If it's behind a firewall or proxy, ensure that outbound connections to the AWS IoT Core endpoint (either public or your private VPC endpoint) are permitted on the correct ports (usually 8883 for MQTT/TLS or 443 for HTTPS). Use tools like `ping` or `traceroute` (if available on your device's OS) to see if the network path is clear. If you're using a private VPC endpoint, make sure your device's DNS is resolving the endpoint's address to the private IP within your VPC. This is a very fundamental check, but often overlooked.
For example, try to `ping` the public AWS IoT endpoint from a machine on the same network as your IoT device. If that fails, then you know your issue is likely with the local network or firewall. If it succeeds, but your device still can't connect to your private VPC endpoint, then the problem might be with DNS resolution or routing within your VPC itself. It's a bit like checking if the road is open before you start your journey, basically.
Inspect Security Settings
This is where you double-check your AWS VPC configuration. Look very closely at the security groups attached to your VPC endpoint for AWS IoT Core. Ensure they allow inbound traffic on the necessary ports (like 8883 or 443) from the IP addresses or CIDR blocks where your IoT devices originate. Also, verify the network ACLs (NACLs) on the subnets where your VPC endpoint resides. NACLs are stateless, so you need to allow both inbound and outbound rules for the traffic. It's a rather common mistake to miss one side of the NACL rule, you see.
Make sure that the security group associated with your VPC endpoint explicitly permits traffic from the source IP range of your IoT devices. If your devices are connecting from outside AWS, this means allowing traffic from their public IP addresses. If they're connecting via a VPN or Direct Connect, ensure those network paths are also configured to route traffic correctly to your VPC endpoint. This step is absolutely critical for securely connect remote IoT VPC AWS not working.
Check Device Credentials and Certificates
The security handshake between your device and AWS IoT Core relies heavily on correct certificates and keys. Verify that your device has the correct client certificate, private key, and the AWS IoT root CA certificate. Ensure none of them have expired. A very tiny typo in a certificate file name or an incorrect path can cause a connection failure. Sometimes, too, the device's clock might be out of sync, leading to certificate validation issues. This is a rather subtle point, but it's important.
You should also confirm that the certificate attached to your IoT "Thing" in AWS IoT Core is indeed the one your device is presenting. If you've rotated certificates or provisioned new devices, it's easy to get these mixed up. A quick check of the device's configuration file or embedded code will usually tell you what certificate it's trying to use. This step is often the key to resolving why securely connect remote IoT VPC AWS not working, especially with TLS errors.
Review AWS IoT Core Logs and Metrics
AWS IoT Core provides very helpful logging through CloudWatch Logs. Set up logging for your IoT Core endpoint to capture connection attempts, authentication failures, and authorization errors. These logs are a treasure trove of information, telling you exactly why a connection was rejected or why a message wasn't processed. Look for error messages like "AuthFailure," "ConnectionRejected," or "PolicyDenied." These messages, you know, are usually quite explicit about the problem.
Also, keep an eye on AWS IoT Core metrics in CloudWatch, such as `ConnectAttempts`, `ConnectSuccess`, `ConnectAuthErrors`, and `PublishIn`. A discrepancy between `ConnectAttempts` and `ConnectSuccess` indicates a connection issue, while `ConnectAuthErrors` points directly to credential or policy problems. These metrics give you a high-level view of what's happening, which can be very insightful when securely connect remote IoT VPC AWS not working.
Test Connectivity Incrementally
If you're still stuck, try to simplify the connection path to isolate the issue. Can your device connect to the public AWS IoT Core endpoint? If it can, then the problem is likely with your VPC endpoint setup or private network configuration. If it can't even connect to the public endpoint, then the issue is probably with the device itself, its certificates, or the local network/firewall. This step-by-step testing, basically, helps narrow down the possibilities quite a bit.
You could also try using a simple MQTT client on a computer within your VPC (or a test device outside your firewall) to connect to your VPC endpoint. If that works, then your VPC endpoint and AWS configurations are probably fine, and the issue points back to your specific IoT device or its immediate network environment. This kind of controlled testing, you know, is very effective for pinpointing the exact failure point.
Use VPC Flow Logs and CloudWatch
VPC Flow Logs capture information about the IP traffic going to and from network interfaces in your VPC. Enable Flow Logs on the network interfaces associated with your VPC endpoint and analyze them in CloudWatch Logs or S3. Look for "REJECT" entries that indicate traffic being blocked. This can tell you if your security groups or NACLs are indeed blocking the connections from your IoT devices. It’s a very powerful diagnostic tool for network-related issues, honestly.
Combine Flow Logs with CloudWatch metrics for your network interfaces. You can see packet drops or unusual traffic patterns. If you see traffic hitting your VPC endpoint but then being rejected, Flow Logs will often tell you why, perhaps due to a security group rule or a routing issue. This level of detail is often what's needed to truly understand why securely connect remote IoT VPC AWS not working, especially when network configuration is suspected.
Best Practices for Secure IoT-VPC Connections
Beyond just troubleshooting, there are some really good ways to set up your IoT-VPC connections so they are secure and reliable from the start. Thinking about these things upfront can save you a lot of headaches down the line. It's about building a solid foundation, you know, so things just work smoothly.
Employ PrivateLink for VPC Endpoints
Always, always use AWS PrivateLink for your VPC endpoints to connect to AWS IoT Core. This keeps your device traffic entirely within the AWS network, never touching the public internet. This significantly reduces the attack surface and provides a much more secure and predictable connection. It’s a very strong recommendation for any production IoT setup. You know, privacy is key here.
By using PrivateLink, you're essentially creating a private connection between your VPC and the AWS IoT Core service. This means your data doesn't have to traverse public routes, which can be less secure and less reliable. It's a bit like having a private, dedicated highway for your IoT data, which is rather good for both security and performance.
Implement Strong Authentication and Authorization
Don't rely on weak authentication methods. Use X.509 client certificates for device authentication with AWS IoT Core. For authorization, employ fine-grained IAM policies that follow the principle of least privilege. This means giving your devices only the permissions they absolutely need, and nothing more. This is a very fundamental security practice that should never be skipped. That, in fact, is how you keep things tight.
For example, if a device only needs to publish data to a specific topic, its IAM policy should only allow `iot:Publish` on that one topic. It shouldn't have permissions to subscribe, receive, or publish to other topics. This limits the damage if a device's credentials are ever compromised. It’s about minimizing risk, basically, and keeping your system as resilient as possible.
Segment Your Network Thoughtfully
Within your VPC, organize your resources into different subnets and apply appropriate security groups and NACLs. For instance, put your VPC endpoint in a private subnet and ensure only necessary traffic can reach it. This network segmentation helps contain potential security breaches and makes it easier to manage traffic flows. It's like having different rooms in a house, each with its own lock, rather than just one big open space, you know.
Consider using separate subnets for different types of IoT devices or different stages of your IoT pipeline. This allows you to apply distinct security policies to each segment, making your overall architecture more resilient. It's a rather strategic approach to network design that pays off in terms of both security and manageability, especially as your IoT fleet grows.
Automate Deployment and Configuration
Manual configuration is prone to errors. Use Infrastructure as Code (IaC) tools like AWS CloudFormation or Terraform to define and deploy your VPC, subnets, security groups, VPC endpoints, and IoT resources. This ensures consistency, repeatability, and reduces the chance of human error. Automation, you see, is a very powerful way to maintain order in complex systems.
Automating your deployments means that every time you set up a new environment or add new devices, the configuration is exactly the same, reducing the likelihood of subtle misconfigurations that lead to problems like securely connect remote IoT VPC AWS not working. It also makes it much easier to roll back changes if something goes wrong, which is a rather nice safety net.
Monitor Constantly
Set up continuous monitoring for your IoT connections and VPC. Use AWS CloudWatch Alarms to get notified about connection failures, authentication errors, or unusual traffic patterns. Regular monitoring helps you detect issues quickly, often before they become major problems. This proactive approach, you know, is essential for keeping your IoT solution running smoothly. Learn more about CloudWatch monitoring on our site.
Implement dashboards that give you a clear view of your IoT device connectivity status and data flow. Look for spikes in connection attempts without corresponding successes, or drops in message rates. These are often early indicators of a problem. Being able to visualize these metrics helps you stay on top of things, and it's rather important for maintaining a healthy IoT ecosystem. You can also link to this page here for more details on advanced logging.
When All Else Fails: Seeking Deeper Help
Sometimes, even after going through all the troubleshooting steps, you might still find yourself in a tricky spot where securely connect remote IoT VPC AWS not working. That's perfectly fine, you know, some problems are just a bit more stubborn than others. Don't feel bad about reaching out for a little extra help when you've exhausted your own efforts. It's a rather smart thing to do, actually.
If you have an AWS Support plan, opening a detailed support case is often the next best step. Provide them with all the information you've gathered: logs, error messages, configuration details, and the steps you've already taken. They have deeper insights into the AWS services and can often spot something you might have missed. They are, basically, the experts for this kind of thing.
Engaging with the AWS developer community forums or specialized IoT and networking forums can also be very beneficial. Other users might have encountered similar issues and can offer fresh perspectives or solutions. Sometimes, just describing your problem to someone else helps you think about it differently, you know. There's a lot of collective wisdom out there, and it's rather good to tap into it.
For particularly complex or mission-critical deployments, considering an AWS Partner or a specialized cloud consultant might be a good idea. They have extensive experience with intricate AWS architectures and can provide tailored advice and hands-on assistance. This can be a very effective way to get past those really tough connectivity puzzles, especially when time is of the essence. You want to get those devices talking, after all.
Related Resources:


Detail Author:
- Name : Deja Langosh
- Username : damion88
- Email : nathanial06@boyle.com
- Birthdate : 1972-12-24
- Address : 91959 Velma Fort Lake Tara, OR 10725
- Phone : +1 (956) 805-0848
- Company : Schumm Inc
- Job : Crossing Guard
- Bio : Fugiat autem qui qui rerum sit ad molestias. Qui ipsum error vel est. Quisquam et nihil dolore. Iure sit quos unde est necessitatibus quia.
Socials
facebook:
- url : https://facebook.com/wava_dev
- username : wava_dev
- bio : Harum deleniti maiores aut. Est soluta asperiores dolor.
- followers : 2707
- following : 823
twitter:
- url : https://twitter.com/wava_parker
- username : wava_parker
- bio : Soluta quia ducimus beatae repellat. Et eaque modi deleniti expedita.
- followers : 3758
- following : 2968
tiktok:
- url : https://tiktok.com/@parkerw
- username : parkerw
- bio : Sed quibusdam perspiciatis tempora nemo velit voluptas impedit.
- followers : 4698
- following : 2389
instagram:
- url : https://instagram.com/wava_official
- username : wava_official
- bio : Quo consequatur consectetur eveniet praesentium. Dolores qui consequuntur nostrum voluptatem nisi.
- followers : 4116
- following : 2035