You know, sometimes a name can really spark curiosity, can't it? When you hear something like "Pam Bondi have children," it's pretty natural to wonder about the lives of folks who have been in the public eye. People often look for details about well-known individuals, perhaps their family life, or what they're up to these days. That kind of human interest is, like, a very natural thing, really.
But what if that initial thought leads us somewhere a little different, yet equally important? What if the "PAM" we're thinking about isn't a person at all, but something vital for our digital safety? As a matter of fact, there's a really significant concept in the world of technology that goes by the acronym PAM, and it's all about keeping our digital information safe and sound.
So, while the name Pam Bondi might bring up thoughts of a public figure, we're actually going to talk about something that helps protect organizations from online dangers, something called Privileged Access Management. It's a pretty big deal for keeping digital systems secure, you know, and it's something everyone who uses computers should probably understand a little better.
Table of Contents
- What is Privileged Access Management (PAM)?
- Why PAM Matters for Digital Safety
- How PAM Works in Practice
- The Role of PAM in Identity Security
- PAM for Special Digital Environments
- Protecting What Matters Most with PAM
- Frequently Asked Questions About PAM
What is Privileged Access Management (PAM)?
Privileged Access Management, or PAM for short, is essentially a clever security approach. It's a solution that really helps organizations guard against unwanted digital threats. You see, it does this by watching very carefully, spotting unusual activities, and stopping anything unauthorized from happening. It's a bit like having a really good security guard for your most sensitive digital areas, so to speak.
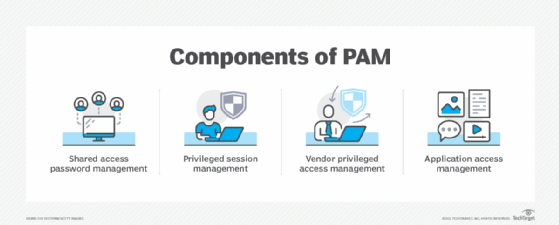
This PAM thing, it actually involves a set of digital security methods and special tools. These tools are all about gaining control over those special, elevated permissions that certain digital identities and users have. Think of it this way: some digital accounts have "keys to the kingdom," and PAM helps manage who gets to hold those keys, and what they can do with them. It's pretty important, frankly, for keeping things in order.
In some respects, PAM is a specific kind of identity management, and it's a key part of cybersecurity. Its main focus is on keeping an eye on, managing, and shielding those special accounts within a digital system. These are the accounts that have extra powers, so to speak, and PAM makes sure those powers are used only when they should be. This is, you know, a pretty big deal for overall digital health.
Why PAM Matters for Digital Safety
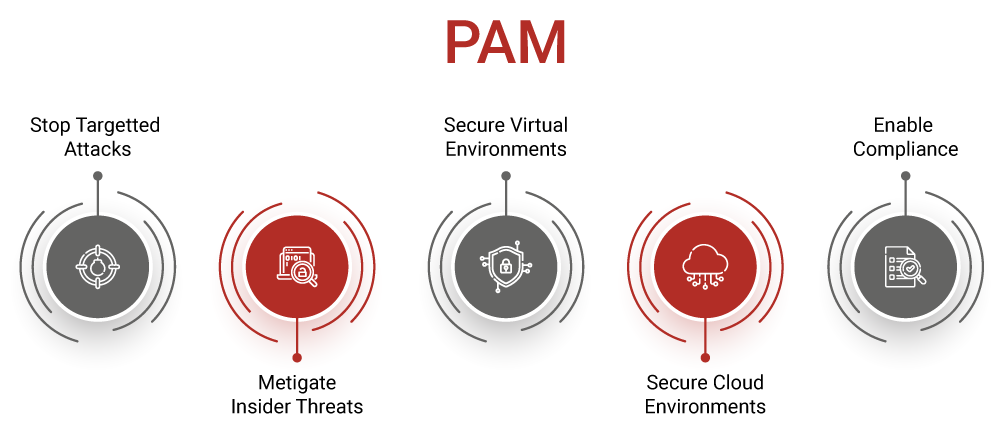
So, why is PAM such a big deal, you might ask? Well, it truly helps organizations manage and secure access to their most important digital systems, applications, and all their valuable information. These sensitive parts of a system are typically only for those special accounts, the ones with extra permissions. Without PAM, those sensitive areas could be, arguably, more vulnerable.
PAM is, in a way, a cybersecurity game plan and a collection of tools. These are all aimed at protecting an organization's most sensitive information and its critical digital systems. It does this by very carefully controlling and monitoring who gets to access these vital parts. It's about being really precise with who has the right to do what, which is pretty essential for keeping things safe.
You see, Privileged Access Management is a security structure that's put in place to shield organizations from those pesky online dangers. It does this by controlling and keeping a close watch on who can get to critical information. It's like having a very clear set of rules about who can enter a secure room and making sure those rules are always followed. This is, quite frankly, a foundational piece of modern digital protection.
How PAM Works in Practice
When you get down to it, Privileged Access Management works by figuring out who, what processes, and what technology really need those special, elevated access rights. It then sets up clear guidelines and rules to make sure those sensitive digital resources are kept safe within an organization. It's about drawing clear lines and making sure everyone understands them, which is, you know, a good way to operate.
For instance, it might mean that a system administrator only gets full access to a critical server for a short time, just when they need to perform a specific task. Once that task is done, their special access is automatically taken away. This way, if their account were to be compromised, the damage would be, arguably, much more limited. It's a very smart way to reduce potential risks, as a matter of fact.
PAM also keeps a detailed log of every action taken by privileged accounts. This means if something goes wrong, or if there's an audit, you can see exactly who did what, and when. This kind of transparency is, literally, invaluable for security and accountability. It helps everyone stay on the right track, and it provides a clear record if there's ever a question about something.
The Role of PAM in Identity Security
PAM is a cornerstone of identity security, which is all about making sure that only the right people and systems have access to the right things. It's a way to make sure that digital identities, whether they belong to a person or a machine, are used properly and securely. This is, you know, a pretty fundamental part of protecting any digital setup today.
It's not just about stopping outside attackers, either. PAM also helps prevent issues from inside an organization, like accidental mistakes or even intentional misuse of power by someone who has too much access. By limiting access to only what's absolutely necessary, it reduces the chances of either of those things happening. This is, frankly, a huge benefit for any business.
Think about it like this: if only a few people have the master key to a building, and those keys are carefully tracked, the building is generally safer than if everyone had a master key. PAM applies that same idea to the digital world. It's about making sure the "master keys" to your digital systems are very well protected and only used by those who truly need them, and only when they need them. That's, actually, a pretty simple way to look at it.
PAM for Special Digital Environments
There are even specific kinds of PAM solutions for particular situations. For example, there's a type called MIM Privileged Access Management. This solution is really good at helping organizations put limits on special access within an existing and isolated Active Directory environment. It's designed to work with what's already there, which is, you know, often very helpful for businesses.
This kind of specialized PAM can be especially useful for larger organizations that have complex digital setups. It helps them tighten security without having to completely rebuild their existing systems. It's about adding a layer of protection that fits right in, making things safer without causing too much disruption. That's, arguably, a very practical approach to security.
So, whether it's a standard network or a more specific setup, PAM tools are designed to adapt and provide that crucial layer of control. They help ensure that even in unique digital spaces, those with elevated permissions are properly managed and monitored. This means a lot for peace of mind, really, knowing your digital assets are better protected.
Protecting What Matters Most with PAM
At its core, PAM is about safeguarding an organization's most sensitive data and critical systems. It does this by very carefully controlling and watching over those who have special access. It's a bit like having a very vigilant guardian for your digital treasures, making sure no one gets to them who shouldn't, or does something they shouldn't. This is, you know, a pretty comforting thought for any business owner.
The goal is to prevent unauthorized actions that could lead to data breaches, system downtime, or other serious problems. By having strong policies and technologies in place, PAM reduces the risk of these things happening significantly. It's about being proactive rather than reactive, which is, basically, always a better way to handle security.
So, while the initial thought of "Pam Bondi have children" might be about personal lives, the "PAM" we've explored here is about the digital lives of organizations. It's a critical tool in today's connected world, helping to ensure that the digital systems we rely on every day remain secure and trustworthy. It's, truly, a very important part of our shared digital future.
Frequently Asked Questions About PAM
What is the main purpose of Privileged Access Management?
The main purpose of PAM is to protect organizations from online threats by carefully watching, spotting, and stopping any unauthorized access. It helps control who gets to use special accounts that have extra powers within a digital system. It's, you know, about keeping those powerful accounts safe and sound.
How does PAM help protect against cyberthreats?
PAM helps protect against cyberthreats by making sure that access to critical systems and sensitive information is tightly controlled. It monitors what people with special access are doing and can prevent them from taking actions that aren't allowed. This reduces the chances of a security incident, which is, frankly, a huge benefit.
Can PAM be used in any type of organization?
Yes, PAM can be used in pretty much any type of organization, from small businesses to very large enterprises. Any organization that has digital systems and sensitive data can benefit from the added security that PAM provides. It's, actually, a good idea for anyone serious about digital protection.
To learn more about digital security on our site, you can explore various topics. Also, you might find more helpful information on cybersecurity best practices by checking out this page.
For more general information about cybersecurity and how it protects organizations, you can always check out resources like the Cybersecurity & Infrastructure Security Agency (CISA) website. They have, like, a lot of good stuff there.
Related Resources:

Detail Author:
- Name : Alverta Blick
- Username : bkautzer
- Email : jess79@hotmail.com
- Birthdate : 1972-02-23
- Address : 165 Jessy Lake West Araceli, WI 41105-5678
- Phone : 315.762.7576
- Company : Bogisich, Bauch and Beatty
- Job : Transportation Worker
- Bio : Eos labore qui quas at odit. Natus dolor enim aut et explicabo eius unde incidunt.
Socials
twitter:
- url : https://twitter.com/zulauf2023
- username : zulauf2023
- bio : Nisi vel quia alias iusto odit asperiores. Voluptatem saepe voluptates et incidunt.
- followers : 6575
- following : 2702
instagram:
- url : https://instagram.com/zulauf1984
- username : zulauf1984
- bio : Rem laborum quae deserunt. Quisquam enim fugiat neque. Voluptas rerum quibusdam qui unde saepe.
- followers : 140
- following : 2334
linkedin:
- url : https://linkedin.com/in/martinazulauf
- username : martinazulauf
- bio : Maxime ut repellendus adipisci nulla.
- followers : 6787
- following : 258
tiktok:
- url : https://tiktok.com/@martina_zulauf
- username : martina_zulauf
- bio : Laboriosam expedita et qui iusto optio illum eaque tenetur.
- followers : 6395
- following : 1875